Hash algorithms — blockchain fundamental
[82/100] days of web3 challenge

[82/100] days of web3 challenge
📌 how it works?
📌 why is it a great solution for blockchain?
📌 different kind of algorithms.
🚀 Do you know the answers for all of this questions?
~ if not, this tutorial is for you.
Hash is a crucial part of each blockchain which holds entire decentralization and results as a great solution for finances, proof of ownership, digital ozone assets.
Each blockchain can use different solutions, other functions and their advantages. However, do you know what exactly is a hash algorithm?
Agenda:
- intro,
- what is it,
- how it works,
- different hashing functions,
- conclusion.
What is it?
Hash algorithm is literally a function which takes as an input some amount of dat (practically to this function can be passed a lot of variables) and returns a fixed output called hash.
This hash is a string which length is always the same, no matter how many variables will be passed.
Moreover, only one tiny change in inputs can dramatically impact on the final result.
There you can find an entire material about role of the hash in a blockchain:
How it works?
Before explaining fundamentals of bitcoins sha256 algorithm, let’s see how it behaves in a simulator.
Below is presented a preview:
Below are presented steps of sha256 algorithm:
1. add to input 64 and as many bits to achieve the result which can be divided by 512.
Input bits + needed bits + 64= n*512
Added bits should start with 1 and filled with zeros, like:
1000000
2. Initializing buffers.
There are needed 64 default values to perform hashing, like:
a = 0x792c78gh
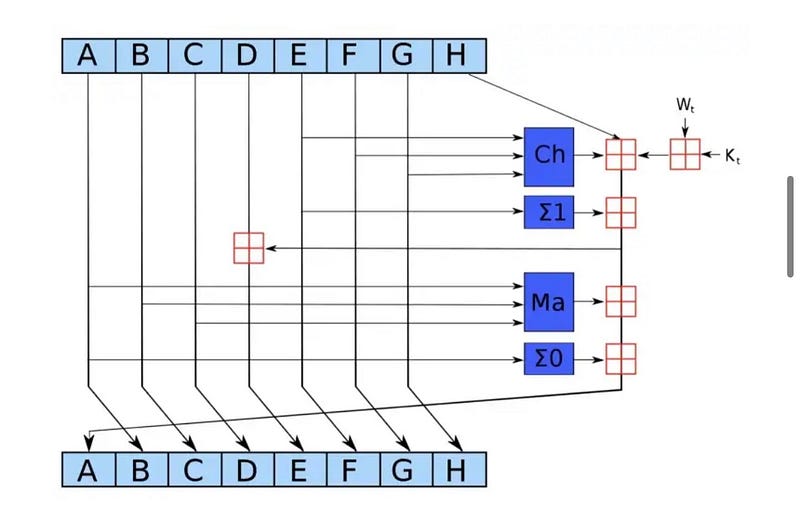
3. Compression function.
The entire string is divided into n amount of 512 bits variables, according to the first step.
This chunks are going 64 times through the operation. What is more, an output of previous iteration is an input in next.
Single round operation can be very complex and looks like in the schema below:
The very good resource for deep understanding is presented below:
5. Getting output
Output is irreversible, so that there is no way to crack it and receive inputs in some kind of an operation.
The very simple example of irreversible function is a modulo.
It is well described in my previous thread about asymmetric cryptography:
Examples
Below are presented the most famous examples:
- MD5,
- SHA-1,
- SHA-2,
- NTLM,
- and LANMAN
Conclusion
Hash algorithms are one of the best tools to achieve fully secured program, which will be encrypted and not vulnerable for some cyber attacks. That is why, bitcoin network begin to use it and revolutionalized the approach for these kind of functions.
Do you like my web3 content? Follow the repo which consists all of the topics from a challenge: